Gargoyle Investigator MP Datasheet 
- Advanced malware discovery
- Used by forensic labs, law enforcement, field investigators, private investigators, and incident response teams
- Rapid search of malicious applications
- Comprehensive reporting
GET A FREE TRIAL

Gargoyle Investigator™ MP is the next generation of WetStone’s advanced malware discovery solution for computer forensic investigators and incident response teams. It is designed for forensic laboratories, law enforcement, field investigators, advanced private investigators, and enterprise cyber security personnel. Gargoyle performs a rapid search for malicious applications and provides significant clues regarding the activities, motives and intent of a suspect.
Gargoyle Investigator™ MP takes everything that its current users know and love about Gargoyle Investigator and improves upon it. Its new, modern codebase, faster scan times, and improved archive and file format processing make Gargoyle Investigator™ MP a great improvement over the previous generation of Gargoyle Investigator™.
Gargoyle MP is designed to simplify your breach and malware triage investigation and incident response activities. Gargoyle MP enables users to perform a rapid search for known contraband, hostile programs and lost or leaked corporate assets.
Understanding the impact of malicious code is essential when conducting cyber crime investigations, whether it is the discovery of botnets, trojans, anti-forensics, mobile malware or a host of other malicious applications. Accessing the full intent, sophistication, capabilities and communications of cyber criminals requires a complete understanding of what is in play.
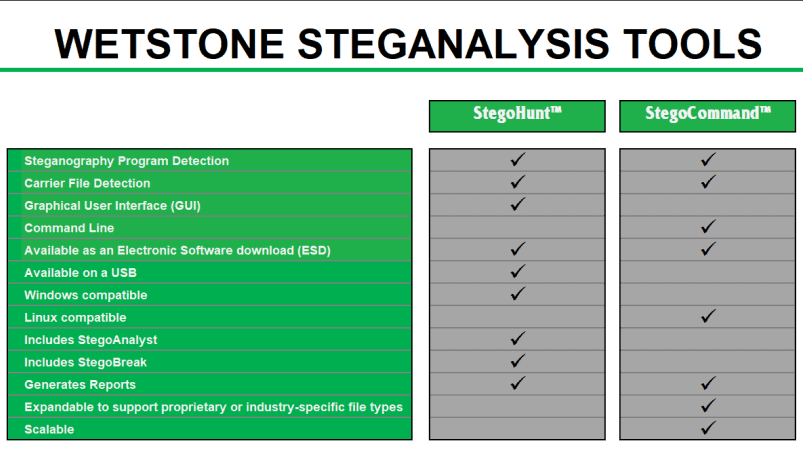
Gargoyle MP is designed to integrate with EnCase by Guidance Software and AccessData’s Forensic Toolkit (FTK) to streamline the process of performing investigations on live machines or forensic images. Users can utilize a WetStone Technologies-provided EnScript inside EnCase in order to create a hash file of all files present on an image. This hash file can then be used for advanced malware discovery using Gargoyle MP.
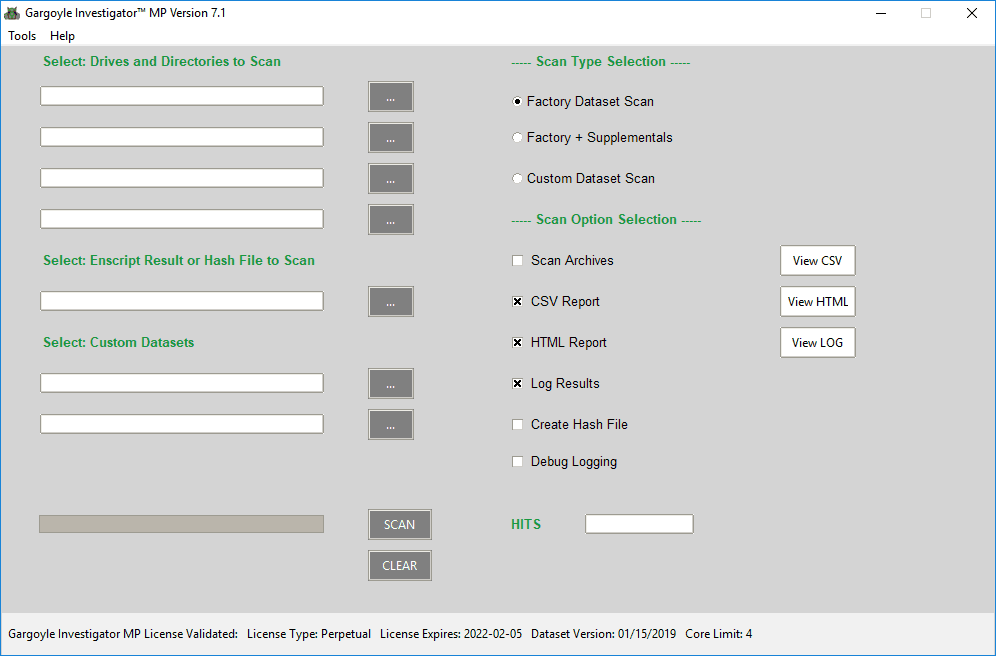
Gargoyle MP provides comprehensive reporting in both HTML and CSV formats for use as digital evidence. Reports are generated in HTML format for an at-a-glance understanding of the threats identified on a system. Within the HTML report program detections are classified by program category, with a comprehensive table of pertinent information provided for each detected file. Gargoyle also produces a CSV report, with all the same detection data, for use in parsing engines or other custom applications.
Gargoyle MP also gives users the option to generate a case file at the time of the scan. When selected, the program will generate a CSV file in the same format as the WetStone EnScript file. This gives the user the ability to re-scan a system later in the future.
FEATURES OF GARGOYLE INVESTIGATOR™ MP
- Advanced malware discovery
- Used by forensic labs, law enforcement, field investigators, private investigators, and incident response teams
- Rapid search of malicious applications
- Comprehensive reporting
- Compatible with a variety of Windows desktop platforms:
- Windows 7
- Windows 8
- Windows 8.1
- Windows 10
- Compatible with a variety of Windows Server platforms:
- Windows Server 2008 and 2008 R2
- Windows Server 2012 and 2012 R2
- Windows Server 2016
WHAT TYPES OF PROGRAMS CAN GARGOYLE MP DETECT?
WetStone Technologies searches for and maintains a malware repository for each of the following program categories:
- Anti-forensics
Anti-forensic software is used by suspects to thwart digital forensic investigations. Common capabilities of software in this category include: drive wiping, cache and history erasers, file property and time alterations, VPNs, and e-mail and chat log erasers. Modern versions of these applications can run on a schedule allowing automatic, unattended operation. In addition, execution can be triggered by an event such as system shutdown or start-up.
- Botnet
Botnets are software programs that are designed to execute autonomously as “software robots.” They can be used to remotely control computing resources where the botnet has been installed or infected. Botnets can be orchestrated to launch distributed denial of service attacks, wreak havoc within networks, or simply combine the resources of thousands of computers for a nefarious goal. Investigators that discover botnets during an investigation should determine when the botnet was installed, when it was last accessed, and look for evidence of infection on other networked computers. One important determination is whether the infected computer is the victim or the suspect that is orchestrating the botnet.
- Cryptojacking
Cryptojacking applications are malicious programs that mine for cryptocurrency without the express knowledge or permission of the user. Cryptojacking programs often disguise themselves as benign applications, such as a game, but will mine for cryptocurrency in the background. Compromised websites may also use malicious JavaScript to use the resources of the website visitors’ machines to mine for cryptocurrency. Identifying cryptojacking programs is important to an investigation because it could be an indication that a system is compromised.
- Cryptomining
Cryptomining programs are applications that are used for mining cryptocurrency. Crytpomining programs are installed by the user with the express understanding that the purpose of the program is to use the resources of the machine to mine for cryptocurrency. The identification of cryptomining programs in a forensic investigation could be important if, for example, an employee was using corporate resources for personal financial gain.
- Denial of service
Denial of Service Denial of Service (DoS) and Distributed Denial of Service (DDoS) software are used to overwhelm and disrupt computer and network operations. These cyber-weapons are typically used by hackers to crash websites and internet-based operations. They can also be used to create large volumes of traffic in order to overwhelm network intrusion detection systems.
- Encryption
Encryption software certainly has legitimate and important purposes in protecting personal and proprietary data. Uncovering its use as part of an investigation can provide important information to the investigator regarding both the sophistication of the suspect, as well as the measures put in place to protect potentially incriminating data. In addition, knowing exactly what type of encryption is being employed by a suspect is necessary to potentially recover (through cracking or other means) the encrypted data.
- Exploit Kit
Exploit kits are programs that are designed in order to exploit a known vulnerability in a piece of software or online resource. These tools are often distributed as a package, which will enable attackers with limited sophistication, such as script kiddies, to launch a sophisticated attack.
- Exploit scanner
Exploit scanners are applications which allow users to identify potential security vulnerabilities in a target system. These applications actively seek out, report upon, and even instruct the user as to how to exploit discovered vulnerabilities. Once vulnerabilities have been discovered, the target machine is open to attack from a wide range of malicious software.
- Fraud tools
Fraud tools are used to generate fake credit card, ATM, and calling card numbers. Another use of these applications is to validate stolen or forged credit card numbers; many of these programs provide mathematical validation of card numbers. When the investigation involves financial crimes, the discovery of such card fraud applications may provide critical information to the investigator as to the modus-operandi of the suspect.
- Keylogger
Keyloggers are applications designed to covertly monitor key strokes on an unsuspecting machine. They have the ability to be installed locally or remotely. Both facets pose a risk,since once a machine has been compromised, all key strokes can be monitored. Most keyloggers leave some type of remnant on the file system being monitored; however, there are a few that run in memory and do not write to the file system. Keyloggers are generally installed nefariously; however, some organizations install the application to monitor employee activities.
- OSINT
OSINT tools are used to gather intelligence on users or organizations for the purposes of social engineering or reconnaissance. These tools may be used to gather information in order to launch a more targeted, sophisticated attack, such as spear-phishing, on the target.
- Password cracking
Password cracking tools are designed to break password-protected files and accounts. There are legitimate reasons to have such a tool, particularly a commercial version, from a system administration perspective; however, most of the freeware tools in this category are not designed for system administration. Passwords are a secure way to protect private information. These tools allow for a way to obtain this private information. This may be a user login to a secure server that runs a company’s entire trading website, or simply an accountant’s personal login to her laptop. Password cracking tools not only try to crack user account passwords, but they also crack specific application-based files. This will allow people without the proper permission to see proprietary or incriminating data.
|
- Peer-to-peer
Peer-to-Peer (P2P) applications are designed to allow for the sharing of files over the Internet. This is a concern because people can anonymously share worms, trojans, and malicious software. They can also be used to covertly smuggle proprietary data outside a network. People associated with child pornography can use this type of tool to share pictures and website locations with others interested in this crime. Sometimes these applications are associated with network vulnerabilities and copyright infringement.
- Piracy
Piracy applications allow users to bypass copyright protection in various forms of media. The user then has the ability to make an illegal copy of the media and save it to a storage medium. Piracy programs are designed to work with a variety of types of media, including video, audio, and software.
- Ransomware
Ransomware programs are malicious software applications designed to encrypt a user’s files for the purpose of the user paying a ransom to have their files decrypted. Often, the malicious program’s author does not actually decrypt the user’s files, even if they pay the ransom. Ransomware programs have become increasingly popular in recent years. A ransomware outbreak can render an organization’s computer systems useless if the machines are encrypted.
- Remote access
Remote access programs are designed to give users complete control over a particular system from a remote location. This includes everything from viewing files to executing applications remotely. This type of program is especially dangerous as the intruder needs no physical access to the target machine to control it. Thus, any type of data available on the target computer can compromised.
- Rootkit
Rootkits are malicious applications designed primarily to help potential attackers gain root access to a particular computer system. This is accomplished through the masking of various malicious actions occurring on a target machine. These masked actions include things such as running processes, files, and open ports. The two primary modes of operation for rootkits are either direct kernel object manipulation or API hooking.
- Scareware
Scareware encompasses several classes of software, often with no benefit, that are sold to consumers by certain unethical marketing practices. The selling approach is designed to cause shock, anxiety, or perception of a threat, generally directed at an unsuspecting user. Some forms of spyware and adware use scareware tactics. A frequently-used tactic is to convince users that their computer is infected with malware and then suggest that they download, and pay for, anti-virus software to remove it. Usually the malware “threat” is entirely fictional and the downloaded software is non-functional or malware.
- Sniffer
Packet sniffing programs are used to capture and analyze network traffic. Most corporations have policies restricting the use of these applications to authorized personnel. Many protocols, including FTP and chat, are not encrypted. In addition to obtaining cleartext information, collected packets can be used to crack network passwords and find protected files, servers, and user accounts. Investigators need to look for the targets of the attacks and determine what other actions the suspect has performed. It is likely that password cracking tools and binary editors will also be found in addition to packet sniffers.
- Spyware
Spyware applications are expanding in use today from the traditional spousal spying to industrial espionage, unauthorized monitoring, and collection of proprietary data. Discovering the presence of these apps during an investigation can be vital and may reveal information about co-conspirators, along with the sources of data leaks.
- Toolkit
Toolkits enable unsophisticated users to construct new malware applications which may not be detectable by standard signature-based virus scanning engines or hash-based malware scanners. Several generations of tools could be created by changing a couple lines of code. Toolkits provide a wealth of low-level utilities to allow systematic hacking of a computer or network. Users of these tools are often just “playing” with the available functions to see if they can write a virus. However, a more experienced or skilled user could use toolkit features to assist with the deployment and distribution of more malicious applications. Investigators need to assess the sophistication of the suspect to determine their capabilities, and then look for the application created with the toolkit. Hashes of the application installers and executable files should be obtained and made publicly available to other investigators in situations where the malware may have been released.
- Trojan
Trojans are planted on a system to cause damage or open backdoors. A backdoor describes code that is used to give its creator covert and unauthorized access to computers on which the code is running. Usually, a trojan gets installed based on the actions of a user—e.g., clicking on an email attachment. When investigating an identified trojan, the method of infection must be determined as well as the actions and possible backdoors enabled by the program. Suspects have been known to use the “Trojan Defense” to argue that a Trojan somehow was installed and opened a backdoor to allow other activities, such as downloading child pornography, to occur.
- Web threats
Web threat applications consist of malicious server-side or other web-related scripts (PHP, ASP, JSP, etc.). Web threat scripts are uploaded to a web server in order to be used as a backdoor. This category also includes malicious payload exploits used against the browser.
- Wireless tools
Wireless surveillance applications are used to monitor, map and potentially exploit wireless networks and their vulnerabilities. Corporate IT personnel may use some of these tools to verify wireless coverage areas or look for rogue access points. After collecting wireless information, cracking tools can be used to gain access to protected networks. During an investigation, the purpose the suspect had for using the wireless tools needs to be identified. Scans for additional malware categories will provide direction toward the intent of the suspect after obtaining network access.
|
INTEGRATIONS
Gargoyle has the ability to scan comma separated value files, commonly referred to as CSV files of MD5 Hashes. The format of the file is both simple and strict. This allows Gargoyle to scan hash results for malicious code or cyber weapons from virtually any forensic collection platform.
Gargoyle currently integrates with the following platforms:
Encase® Forensic by Guidance Software
WetStone includes an EnScript with Gargoyle Investigator MP. The EnScript will export a hash file from EnCase that will be formatted as comma-delimited file that has the hash file field definitions Gargoyle can scan.
Forensic Explorer by GetData
WetStone allows for an export file from Forensic Explorer to be selected in the hash file section of the user interface of Gargoyle. Gargoyle will then automatically format the data into the hash file field definitions Gargoyle recognizes before it scans the file.
DELIVERABLE
- Your choice of either Electronic Software Download (ESD) or FLASH license type (USB device) for Gargoyle MP
- Access to monthly Dataset updates
- Customer support portal account
- 1-year software maintenance
LICENSING TYPES
- ESD: Electronic software download for use on a single system. Available as a subscription license. Not transferable. Basic license is 2 cores, additional core licensing available.
- FLASH: 16GB USB 3.0 device for use in field investigations, and on multiple systems. Limited to 2 cores.
GET A FREE TRIAL